How to Bypass Right Click Block on Any Website (Hack) - Software Bazar Blog
in
HOW-TO GUIDES,
WEB HACKING
- on 09:27
- 1 comment
In order to block the right-click
activity, most websites make use of JavaScript which is one of the
popular scripting languages used to enhance functionality, improve user
experience and provide rich interactive features. In addition to this,
it can also be used to strengthen the website’s security by adding some
of the simple security features such as disabling right-click, protecting images, hiding or masking parts of a web page and so on.
How JavaScript Works?
Before you proceed to the next part
which tells you how to disable the JavaScript functionality and bypass
any of the restrictions imposed by it, it would be worthwhile for you to
take up a minute to understand how JavaScript works.
JavaScript is a client side scripting
language (in most cases), which means when loaded it runs from your own
web browser. Most modern browsers including IE, Firefox, Chrome and
others support JavaScript so that they can interpret the code and carry
out actions that are defined in the script. In other words, it is your
browser which is acting upon the instruction of JavaScript to carry out
the defined actions such as blocking the right-click activity. So,
disabling the JavaScript support on your browser can be a simple
solution to bypass all the restrictions imposed by the website.
How to Disable the JavaScript?
Here is a step-by-step procedure to disable JavaScript on different browsers:
For Internet Explorer:
If you are using IE, just follow the steps below:
- From the menu bar, go to Tools -> Internet Options.
- In the “Internet Options” window, switch to Security tab and click on the button Custom level…

- From the Security Settings, look for the option Active scripting and select the Disable radio button as shown above and click on “OK”.
- You may even select the Prompt radio button, so that each time a page is loaded, you will have the option to either enable or disable the scripting.
For Google Chrome:
If you are using Chrome, you can disable the JavaScript by following the steps below:
- Click on the Chrome “menu” button (on the top right corner) and select Tools.
- From the “Settings” page, click on Show advanced settings…
- Now under Privacy, click on the button Content settings…
- Under the JavaScript, select the radio button which says “Do not allow any site to run JavaScript” and click on “Done”.
For Mozilla Firefox:
Steps to disable JavaScript on Firefox:
- From the menu bar, click on Tools -> Options.
- From the Options window, switch to Content tab, uncheck the option which says “Enable JavaScript” and click on “OK”.
How to Bypass the Right Click Block?
In order to bypass the right-click block
or any other restriction imposed by JavaScript, all you need to do is
just disable it in the browser and refresh the same page, so that it now
reloads without JavaScript functionality. You are now free to
right-click on the page, view its source or even copy any of the images
that you may want to. Don’t forget to re-enable the JavaScript once
again when your job is over. Otherwise lack of JavaScript support may
result in unusual rendering of web pages.
[Emissary Keylogger Full]Hack Remote Computer GMail Facebook Hotmail MSN Account By using Emissary Keylogger
- on 21:00
- 1 comment
- first u must have the emissary keylogger in ur system. and Net Framework installed bcoz keyloggers wont work without this.
- then u have 2 create fake account at google. its use is this when u hack a person his data will be mailed to ur account.
- ok when u do these 2 Now open the the Emissary Keylogger.
- their you can see Gmail User Name. and below it Gmail Password. PUt the gamil account with password their . Bcoz this will confrm itslef that the mails have 2 sent for ths account or not..
- when u put their u can see Test Mail.. just click on it . it will be blink for a minute and then a window will appear and saying "Message has sent. Check your mail." then check ur mail is their a msg recieved from the emissary. if not then try again bcoz u hv enterd the pass or id wrong.
- After it below u can see Server Namme in the bracket will be written "sever.exe" well u can change the name like Nav.exe..NOTe u can only change server but not .exe e.g.. NAv.exe.
- Below that is Interval .. IT means that what u want in how much minutes the mail come to u from the victms pc. i like to give it 3 bcoz this is gud.
- At the End u can see Build Server. just click on it and i file will apear at ur system by then name u have given in server name . and it will be at the same directory where the emissary keylogger is..
- NOW the file is created with u.. Give that file to the victm who u want to hack If he OPens it then he will be hacked..
- If u are worried how can i gave them . Then post it to the free web hosting space like www.mediafire.com
SandBoxie Control 3.76 Full Version Cracked Serials Keys Cracks - SOFTWARE BAZAR
in
Cracked,
Full Version,
Keys Cracks - SOFTWARE BAZAR,
SandBoxie Control 3.76,
Serials
- on 20:34
- 12 comments
sandboxie 3.76 cracked full version free
download
Sandboxie 3.76 , A Tool That runs your programs in an isolated space
which prevents them from making permanent changes to other programs and data in
your computer.It creates a sandbox-like isolated operating environment in which
applications can be run or installed without permanently modifying the local or
mapped drive. An isolated virtual environment allows controlled testing of
untrusted programs and web surfing.
Title:
|
Sandboxie 3.76
|
Filename:
|
sandsetup.exe
|
File size:
|
3.30MB (3,361,776 bytes)
|
Requirements:
|
Windows 2000 / XP
x32/x64/ Vista x32/x64/ Windows7 x32/x64 8
32-bit / 8 64-bit
|
Languages:
|
Multiple languages
|
License:
|
Commercial
Freeware
|
Download Now
sandboxie 3.76 cracked version with mediafire link
Rape Punishment in yemen Indian goverment should implement this law Sentenced to death - SOFTWARE BAZAR
in
Rape Punishment Indian must learn
- on 07:19
- No comments
Pure Justice!
Yemeni soldier executes this rapist in public who was accused of raping and murdering an 11-year old girl, in the capital Sana'a, Yemen, on 06 July, 2009. Indians should learn something from them.
Shari’ah Law is the solution; the Man-made laws are just an illusion. We should not fall for such worldly deception; life is but short, let us adopt the Divine resolution for a perfect constitution.
Al Ghuraba .
Yemeni soldier executes this rapist in public who was accused of raping and murdering an 11-year old girl, in the capital Sana'a, Yemen, on 06 July, 2009. Indians should learn something from them.
Shari’ah Law is the solution; the Man-made laws are just an illusion. We should not fall for such worldly deception; life is but short, let us adopt the Divine resolution for a perfect constitution.
Al Ghuraba .
Uninstall All UnSigned Apps Installation Certification Problem solved hack symbian s60 phones Easy Method
in
All Hacking Tutorials,
Haking,
install unsigned apps,
Symbian phone
- on 23:32
- No comments
If you own a Nokia Symbian S60 phone, you may presumably bear in mind of the very fact that it's not possible to put in applications on that unless they're signed employing a valid certificate. have you ever been making an attempt to put in applications on your S60 third or fifth edition phone however ending up obtaining a certificate error? now and then, this could be extremely annoying, however here may be a good answer to the present problem!
Here during this post, i will be able to show you the way to hack your Symbian S60 third or fifth edition smartphone, therefore on modify the phone’s computer code and utterly bypass the necessary linguistic communication demand. So, once you're finished this just once hack, you ought to be ready to install associatey compatible application together with unsigned and people with an invalid certificate.
Here during this post, i will be able to show you the way to hack your Symbian S60 third or fifth edition smartphone, therefore on modify the phone’s computer code and utterly bypass the necessary linguistic communication demand. So, once you're finished this just once hack, you ought to be ready to install associatey compatible application together with unsigned and people with an invalid certificate.
What is the Need for Signing Applications?
From the third edition forwards, all the Symbian S60 applications need to be signed so as to make sure their integrity, in order that it'd not be doable for a 3rd party to tamper with the applying. Also, linguistic communication ensures that you simply invariably install applications from a trustworthy supply.
However, there are several software package and beta applications that come back unsigned because the developers cannot afford to shop for a symbian certificate. Hence, it may be a true nightmare for the users who need to install such applications on their phones. So, here could be a gradual procedure to hack your phone and for good disable this security feature:
Download HelloOX2 Ofiicial Website.
HelloOX2 is an
excellent tool to hack Symbian S60 3rd, 5th and Symbian^3 smartphones
which makes it possible to install a root certificate by gaining full
access to the phone’s system files. With this capability, you can
install anything you want on your phones without the need to worry about
the annoying certificate error!
The signed version of HelloOX2 demands
for a donation and hence, only the unsigned version is available for
free download. So, if you have the unsigned version, you need to sign it
before installing on your phone. In order to sign any application, you
need to have the certificate and the key file which can be obtained as
follows:
- Go to the OPDA Website, get registered and login to your account.
- Click on the “Apply Certificate” tab, enter the model number and the IMEI of your phone and then click on “Submit and Upload” button.
- It will usually take up 24 hours for your certificate and key file to be generated and uploaded. To check the status of your certificate click on “My Certificate” tab. If the certificate is ready for the download, you will see something as follows:
- Download the certificate and the key file on to your computer. Also download the SisSigner tool to sign your HelloOX2 application.
- Open the SisSigner, load the HelloOX2.sis, certificate and the key file as shown below and click on “Sign”. Leave the “Key File Password” field blank.
- Your HelloOX2 application is now signed and ready for the installation.
-
Install the signed HelloOX2 application on your phone and run it to start the hacking process, which is completely automatic. Within a minute your phone will be hacked. Once this is done, say goodbye to the annoying certificate error and install any application.
I hope you like this post. Express your opinion through comments. Enjoy!!!
Window Phone Nokia Lumia 925 Release Date Specification reviews Price Features Smart Phone
in
Details,
Nokia,
Nokia Smartphone,
Phone,
Price,
Review,
Smart Phone,
Specification,
Window Phone
- on 01:16
- No comments
The New Window Phone from the no 1 Mobile company Nokia Presented Lumia 925
Specification
| Dimension | 129 x 70.6 x 8.5 mm, 78 cc | |
| Weight | 139 g | |
| Battery | Talk time Up to 18 h 20 m, Stand-by Up to 440 h, Music play Up to 80 h, Non-removable | |
| OS | Microsoft Windows Phone 8 | |
| Memory | 16GB built-in, 1GB RAM | |
| Processor | Dual core 1.5 GHz Krait, Qualcomm MSM8960 Snapdragon | |
| Connectivity | Bluetooth v3.0 with A2DP, USB, WLAN (Wi-Fi 802.11 a/b/g/n, dual-band, DLNA, Wi-Fi hotspot), GPRS Class B, EDGE (Up to 236.8 kbps), 3G (HSDPA 42.2 Mbps, HSUPA 5.76 Mbps), LTE, Cat3, 50 Mbps UL, 100 Mbps DL, NFC | |
| Display Size | 768 x 1280 pixels, 4.5 inches, Corning Gorilla Glass 2 Sensors: Accelerometer, gyro, proximity & compass |
|
| Display Colour | AMOLED capacitive touchscreen, 16M colors, PureMotion HD+ ClearBlack display, Multitouch | |
| Operating Frequency / Band |
GSM 850 / 900 / 1800 / 1900 (HSDPA 900 / 1900 / 2100, HSDPA 850 / 900 / 1700 / 1900 / 2100) | |
| Browser | HTML5 | |
| Colors | Black, White, Gray | |
| Entertainment | FM radio, 3.5mm audio jack, MP4/H.264/H.263/WMV player, MP3/WAV/eAAC+/WMA player, Video/photo editor, SNS integration, Games (built-in) | |
| Camera | 8.0 MP, 3264 x 2448 pixels, autofocus, Carl Zeiss optics, optical image stabilization, xenon flash, 1/3" sensor size, 1.4 µm pixel size, PureView technology, geo-tagging, Dual-LED flash, panorama, Video (1080p 30fps), Secondary | |
| Other Features | GPS + A-GPS support and GLONASS, GPU (Adreno 225), MicroSIM card support only, 7GB free SkyDrive storage, Active noise cancellation with dedicated mic, Wireless charging, Document viewer/editor, Predictive text input, Speakerphone | |
| Ring Tones | Downloadable, Polyphonic, MP3, WAV | |
| Messaging | SMS (threaded view), MMS, Email, Push Email, IM | |
Review
Nokia includes a new flagship, and therefore the Lumia 925 comes simply six months when the Lumia 920. With another top-of-the-range handset returning in July, rumours suggest, the 925 may be seen as fixing a number of the issues encountered by the 920 – it shave 46g off to weigh simply 139g. wherever its predecessor was outlined by its heaviness, this new model is amazingly lightweight.
Part of that's right down to a shocking polycarbonate back, that feels each pleasingly tactile and something however flagship, compared to the metal and glass styles of Apple, HTC and even Huawei. It additionally provides a two-tone back, that some individuals can love and plenty of can doubtless not.
Nonetheless, with a rather sq. style, the 925 feels premium overall, and edges from the luxurious look of Windows Phone. A 1.4GHz Snapdrogon processor provides enough oomph, while a 2,000mAh is that the usual, unsatisfactory level which means you would like to plug it in mid-afternoon, and there’s no sd card either. But a 4.5” show with a 1280x768 show is spectacular, there’s currently an FM radio and, as usual, Nokia’s stress on camera performance.
The 925 adds what the Finnish company calls ‘Smart Camera’, that is actually a ‘best shot’ burst mode, taking many and holding you decide on your favorite. It’s a neat plan marred by slightly slow performance. I found I got higher results merely with the quality mode, however, that is superb.
While overall, the Lumia 925 could be a absolutely sensible device, it’s the Windows Phone eight software system that continues to be each its greatest strength and weakness – it's beautiful, however still lacks a number of the apps that ar essential to several users. And it’s a brave client who bets against Apple or android. however if you’re determined to shop for a Windows phone, the Lumia 925 is that the best out there.
Labels:
Details,
Nokia,
Nokia Smartphone,
Phone,
Price,
Review,
Smart Phone,
Specification,
Window Phone
Altaf Hussain[MQM] Faced 7 hours of investigation on money laundering and Dr.Imran farooq killing Case MQM Scotland Yard
in
Altaf Hussain,
fuck,
london hotels,
MQM,
Scotland Yard
- on 10:58
- No comments
LONDON: Muttahida Qaumi Movement (MQM) chief Altaf Hussain has been investigated for over six hours in reference to concealment case by law.
Sources same that Hussain has been summoned for the second spherical of interrogation on seventeenth of this month.
The investigatory agency known as the MQM chief at a police office in Central London.
On the investigation, Altaf was asked queries concerning cash recovered throughout a raid at his residence, property in his name and his supply of financial gain.
The MQM chief same that the property was purchased with donations from party staff and it had been in hand by MQM. He additional same the cash is additionally the donations from the party staff.
According to sources, if the property and cash is proved to be legal, then the case would be resolved against the MQM leader.
Keywords
MQM , Scotland Yard , Altaf Hussain,london hotels ,
Sources same that Hussain has been summoned for the second spherical of interrogation on seventeenth of this month.
The investigatory agency known as the MQM chief at a police office in Central London.
On the investigation, Altaf was asked queries concerning cash recovered throughout a raid at his residence, property in his name and his supply of financial gain.
The MQM chief same that the property was purchased with donations from party staff and it had been in hand by MQM. He additional same the cash is additionally the donations from the party staff.
According to sources, if the property and cash is proved to be legal, then the case would be resolved against the MQM leader.
Keywords
MQM , Scotland Yard , Altaf Hussain,london hotels ,
How to Remove Usage History in Windows 7
- on 22:56
- 1 comment
Some steps to delete the usage history In Window 7
1st Step : delete all temporary files, cookies and internet files.
2nd Step ; Delete all your browsers history Firefox , IE
Internet Explorer
On Explorer Window, click on Tools, then Internet Options and choose Delete all clear all browsing history.
- Cookies: Either delete all by clicking Delete Cookies in the ‘Internet Options’ window or use the File button to delete the ones you want to delete.
- Temp files: Select ‘Delete Files’ to remove them. To manage these files read tips given later in this article.
- Saved form and password data: In the ‘Internet Options’, select Content tab and click AutoComplete. Finally click Clear Forms and Clear Passwords.
Firefox:
Hold ctrl+shift+delete together
and select from the list what you wish to remove i.e. cookies,
passwords, temp files, and form and password data. To delete items one
by one, go to Tools > Options > Privacy > Cookies. Under View Cookies you can choice which ones you want to remove.
3. To remove Recent Items list, click on the Start menu and then click on Recent Options. From the context menu, click Clear recent items.
4. Spybot Search and Destroy is free software you can download that will remove histories stored in registry.
5. Open Spybot and run Check for Problems. It will go through the files and produce a report that shows all the entries. Right-click any one of these and click Select All or you can select one at a time and see for yourself which files you want to keep and which ones to delete.
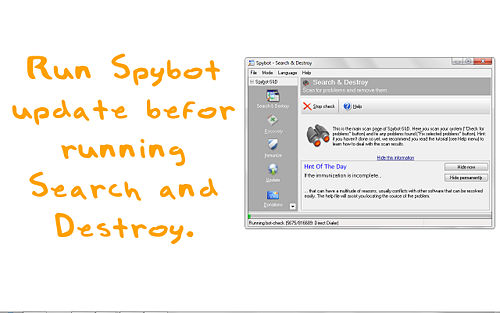
After selection, look for Fix All Problems on the Upper part. Hit that and your files will be removed.
6. At this stage, all your usual history will be deleted. If you still wish to continue and delete the hidden history that only hackers will be interested in then read on. In Windows XP, these are index.dat files that are not saved as text but are programmed in hexadecimal.
7. Open all the index.dat files in your Explorer window. For this purpose, open Windows Explorer and right-click C: drive and first click Search followed by For Files and Folders. Click All Files and Folders and in the name field type “index.dat” afterwards.
You should use More Advanced Options before searching. It will give you the following options to look from:
- Search System Files
- Search Hidden Files and Folders
- Search Subfolders
8. Here you need to alter the files by overwriting the History in index.dat file. You can achieve this by installing PS Pad, a hex file editor.
- First you need to install PS Pad.
- In the index.dat list you ran a search for, if you right-click on any file you will see the option “PSPad Hex” in the menu. Your file will be opened for editing in hex mode. The following screenshot shows how:
- Turn the Read-Only mode off from the file menu of PS Pad first before typing in zeroes in the first available field.
- Use the zero key as much as needed. Overwrite every position by keeping the zero pressed down and navigate to the first listed file. You are also free to overwrite parts of lines of the file by going to that line using scroll bar.
- Once done, save your file and continue to the next index.dat file you want to remove.
Tips
- You can save repetitive work of deleting temporary files by setting your Internet Explorer to remove these files each time you close it. Either change it by going to Tools/Internet Options and looking for the Advanced tab or you can replace your Internet Explorer by Firefox that gives you the option of “Clear Private Data”.
- There are a lot of programs that you can download to save yourself from the entire procedures. You can have any of the softwares like CCleaner, Evidence Eliminator, OSPC Privacy Cleaner, Tracks Eraser Pro, Window Washer or East-Tec Eraser 2007.
- You can disable the Recent Documents option by right-clicking the Start button and going to Properties. From here click Customize under the start menu tab. Go to Advanced look for recent Documents section near the bottom. Here, uncheck “List my most recently opened documents”. If you want to keep the option in start menu then you can use the Clear the List option instead.
- Delete all points in System Restore as well because the registry can be restored to earlier state through this option.
- Eraser is a tool you can install to write the empty space in your hard drive. This will keep your hard drive from a forensic analysis.
- A DNS cache is maintained by Windows so your web pages can be found in less time. Such pages can be listed by opening a CMD window. Click CMD in the ‘run’ box and type ipconfig /displaydns . To clear the cache, type ipconfig /flushdns.
- If you are using somebody else’s computer then ask them before changing any such settings since in many countries, it’s a crime to change computer content.
- Some experts can still restore the data removed in limited situations.
- In some cases, deleting the history data might interfere with management policy. ISPs, Network administrators, and firewalls keep logs.
- Some files you delete might make changes to your system so do it at your own risk.
- If you specifically erase data of your tracks, it might become clear.































